Content
With CMS solutions like WordPress, Joomla, and Drupal, putting together a website is about as easy as building a house out of Lego. No matter what CMS you choose, there are new exploits that are uncovered almost on a weekly basis. This means you need to stay on top of software updates and patches to keep your site secure. Making sure your website is secure should be a top priority. While there are, in fact, many top priorities in website planning, security really does need a lot of attention. A website security review can be done manually or with the ocean of apps and services out there. The options are there and it can be done for a cost or for free, depending on your budget.
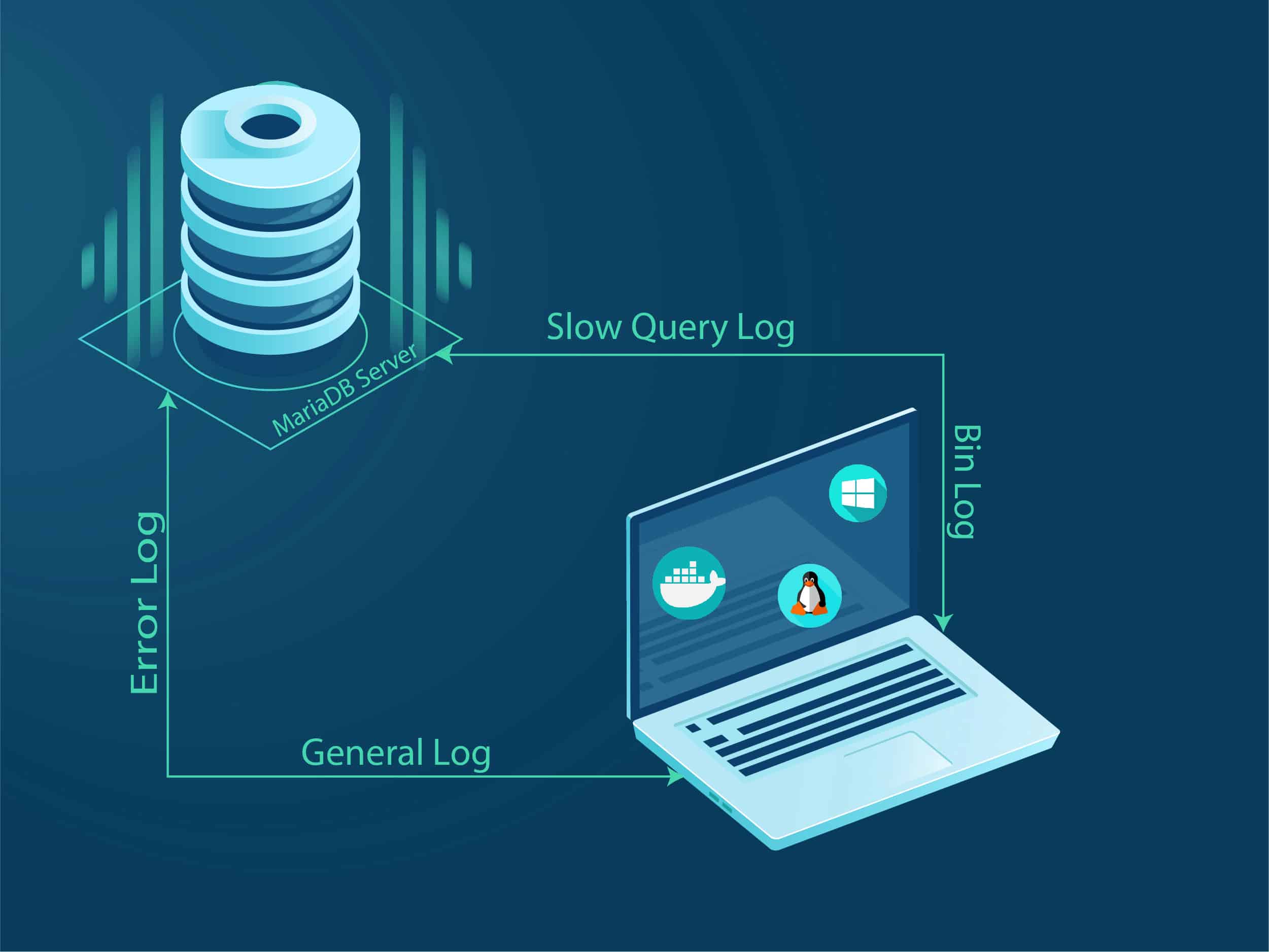
Creating routine backups of your website is not a proactive approach to website security — but it is essential in cases of malicious attacks, hardware failure, or natural disasters. Having a backup of your site means that it can be restored in no time.
What can go wrong if you don’t follow website security best practices?
This can include ransoms for data with complete takeovers, being shut down entirely, redirecting traffic away from the real things, and private customer data being stolen. This happens all too often; you see headlines like ” experiences massive data breach affecting 10 million customers.”
Although this is the ideal situation, it is not always the case. As you would research a plot of land to build a house, you need to examine potential web hosts to find the right one for you. For example, you might use a 14-digit mixture of letters and numbers as a password. You could then store the password in an offline file, a smartphone, or a different computer.
Difference between Flexible, Full and Full (Strict) SSL
This is such an important thing to keep track of and stay on top of, and yet it’s overlooked a lot. For a small website, you can choose a backup plan from your hosting provider. Some of them provide automatic data backups for websites for free, or for a small fee. A big and complex website, on the other hand, requires a huge amount of storage space to save backup data. You can purchase cloud storage to have your data available anytime, anywhere.
Implementing an SSL certificate is a straightforward way you can secure the WordPress admin panel. SSL ensures secure data transfer between your host server and the browser you are using by encrypting the information.
How to make sure a website is secure
How trusting are you of what’s in your phone’s camera roll if you didn’t have some form of security? Keep going through the Rolodex of everyday conveniences we all cosign to the internet without a second thought and you’ll soon realize the scope of the potential issues. There’s an endless list of benefits to having solid website security plans in place, but we’ve chosen a few big items. The most obvious is protecting sensitive data and valuable assets from ending up in the wrong hands. Hackers can “earn” a lot of money by selling off sensitive information to the highest bidders in the deepest bowels of the dark web. Medical record safety, public utility operation, financial information, and much more — can all be compromised and brought to their knees in the blink of an eye. For example, requiring visitors to log in makes perfect sense if your website is a portal for afixed VoIPservice.
- Find out if they have experience using your CMS and if they know what to look for to avoid a security breach.
- Remember when we said it’s a matter of when not if your security will be tested by someone with an agenda?
- You can create backups manually, with a tool, or rely on your hosting provider to do so.
- If you’re on WordPress, many hosting providers offer managed hosting, which takes care of updates for you.
- These are set individually on a per file and per folder basis, although there are ways to bulk update based on type.
- A great example of a default setting change you should make is ‘file permissions.’ You can change the permissions to specify who can do what to a file.
- A website security review can be done manually or with the ocean of apps and services out there.
The third thing you will need to do is to set a free SSL certificate. This is allows you to protect the site and use https instead of just http. You’ll notice how important this is if you visit a unsecured site, chrome will usually give you a large warning and tell you not to visit.
Keep a backup copy of your site
To be double sure that no content on your website can ever be served insecurely, consider implementing a Content Security Policy on your site. To enable this in Cloudflare, go to the Crypto settings and scroll down to the HTTP Strict Transport Security section. Click on Change HSTS Settings, enable all the relevant options and hit Save.
- The problem with just 301 redirecting HTTP traffic to HTTPS is that the initial insecure request still goes over the wire which means it could be read by anyone with access to the traffic.
- Having a backup copy at the very least gives you the peace of mind that if something happens that can’t easily be fixed, you have a fresh copy that works the way it was intended.
- The options are there and it can be done for a cost or for free, depending on your budget.
- They’re not there just for doling out new gimmicks on your iPhone or computer.
- By acting as an intermediary between your web server and visitors to your site, Cloudflare helps to filter out all illegitimate traffic so that only the good stuff goes through.
- Think of your website’s domain name as a street address.