Content
If someone wants data off your device, they can get it if they have physical access to your device. This is the ‘evil maid’ security scenario, named after hotel maids on the payroll of a three-letter agency. If someone has physical access to a laptop – even for an hour or two – the data on that laptop can be considered compromised. Until now, there has been no counter to this Evil Maid scenario, and for good reason. Preventing access to data even when it is in the possession of an Evil Maid is a very, very hard problem.
- It’s not like you have to look far to find examples of poorly implemented systems, or products that are abandoned by their manufacturers and left without critical security updates.
- From CCTV systems to elevator hacks to just about every possible way to defeat a locked door, Deviant has quite a bag of physical security tricks, and he’ll share his insights on keeping stuff safe in a dangerous world.
- [Michal Jirků] found himself in a hotel room with a particularly large gap underneath the door, and decided to quickly design and print a door guard to protect against just such an attack.
- Today, Design Shift has released ORWL, the first computer designed withphysical security in mind.
- I had to build a serial adapter with a breadboard and solid state components to jack my laptop into the wiring harness, and my soldering iron skills leave one with the impression of kindergarten artwork, but it worked.
If you found this interesting or useful, please use the links to the services below to share it with other readers. You will need a free account with each service to share an item via that service.
Automobile Hacking / Vulnerabilities
Many in the community are skeptical about the security of commercial smart home devices, and for good reason. It’s not like you have to look far to find examples of poorly implemented systems, or products that are abandoned by their manufacturers and left without critical security updates. But the design flaw in this video doorbell really drives home how little thought some companies give to their customer’s security. In a phishing, attackers target the ________ technology to so social engineering.
What are the 7 types of hacking?
- 1) White Hat Hackers.
- 2) Black Hat Hackers.
- 3) Gray Hat Hackers.
- 4) Script Kiddies.
- 5) Green Hat Hackers.
- 6) Blue Hat Hackers.
- 7) Red Hat Hackers.
- 8) State/Nation Sponsored Hackers.
Stuxnet, a cyberweapon designed to target Iranian nuclear enrichment facilities, was initially delivered via malicious USB drives. The worm then went on to physically destroy the centrifuges used to refine uranium, showing that cyberattacks can have physical consequences as well as physical delivery. Anyone in the know about IoT security is likely to steer clear of a physical security product that’s got some sort of wireless control. The list of exploits for such devices is a long, sad statement on security as an afterthought, if at all. So it’s understandable if you think a Bluetooth-enabled lock is best attacked via its wireless stack. This whole mess started in August when a gag order was issued against the students’ presentation at Defcon. It’s a shame no one ever saw it because it covers a lot of interesting ground.
The First Evil Maid-Proof Computer
Whether you’re doing security for yourself or a large organization, it’s important to be aware of how physical attacks can compromise assets. Having physical access to a computer opens up new options for an attacker. For example, stealing a password from a well-locked-down computer might be hard to do purely digitally. However, if an attacker is able to physically install a keylogging device, the process suddenly becomes much easier. Supply chain risks is top of mind for cybersecurity teams. Many organizations have started making significant changes to their supply chain security practices over the past year to address growing risks from vulnerable third-party software and open source components.
Is spyware A malware?
Spyware is malicious software that enters a user's computer, gathers data from the device and user, and sends it to third parties without their consent. A commonly accepted spyware definition is a strand of malware designed to access and damage a device without the user's consent.
Download the informative report to learn more about how security teams are mitigating supply chain risks. It doesn’t matter how many bits your password has, how proven your encryption is, or how many TrueCrypt volumes are on your computer.
Now on Hackaday.io
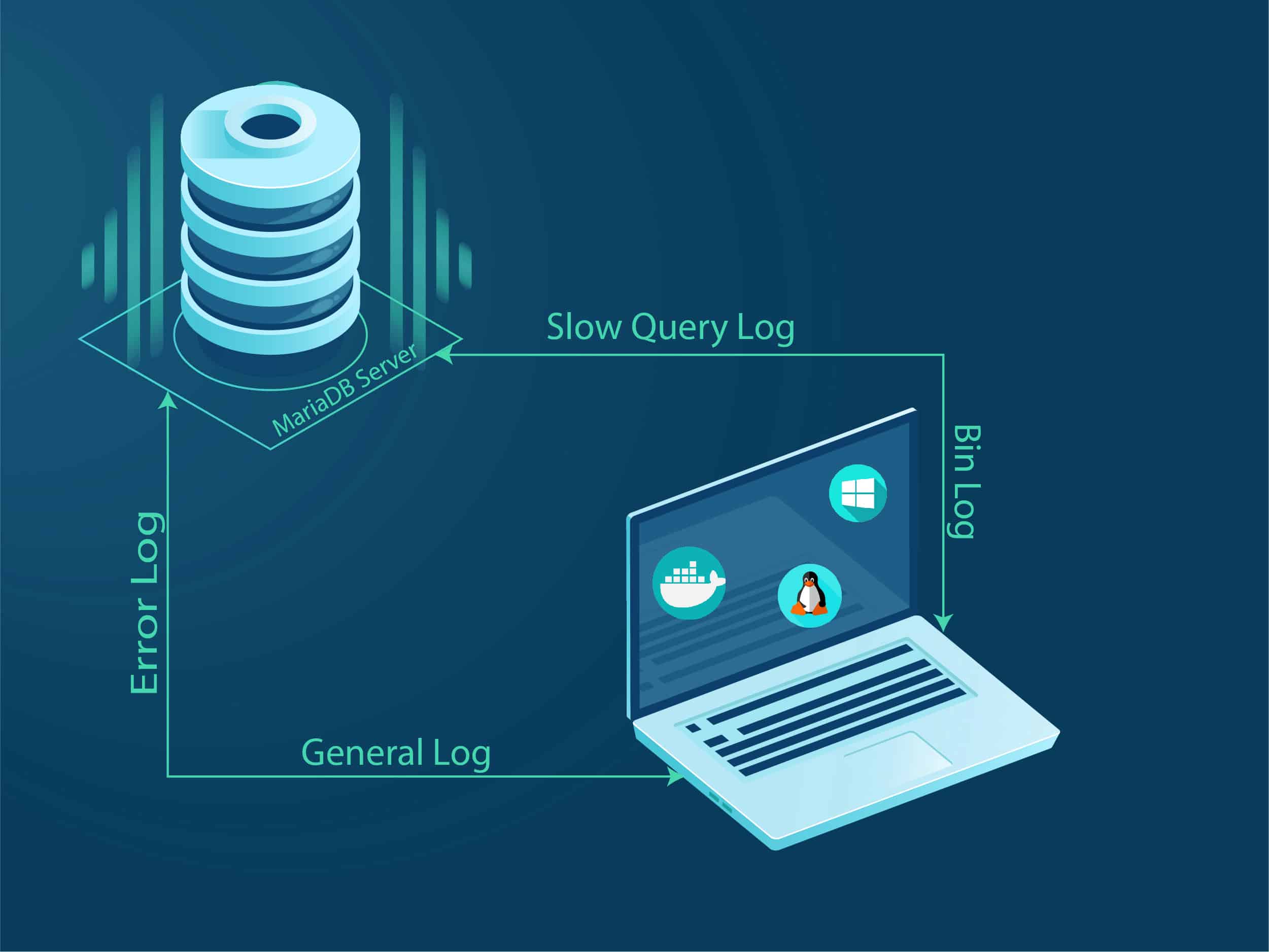
They’re often used for finance or accessing secure areas, and it’s relatively easy to steal information from some types. IT security standards in the United States typically call for physical access to be limited by locked server rooms, sign-in sheets, etc. Surveillance cameras might also be used to deter or detect unauthorized access. Once the black-hats are on the inside, their job becomes orders of magnitude easier. System security starts with physical security, and physical security starts with understanding how to keep the doors locked. But physical security cannot be ignored in the field of cybersecurity.
Memory dump (using tools like dd.exe, mdd.exe, Memoryze, win32dd.exe or DumpIt) to analyze the memory. IT security department must periodically check for security logs and entries made during office hours. ___________ is a special form of attack using which hackers’ exploit – human psychology. “A TURNIP CURES ELVIS” begins the opening credits, an intriguing beginning to a smart and still timely film that was released around 25 years ago. If you’ve never seen the movie, I’m about to spoil the hell out of it.
Hackaday Links: September 18, 2022
The overall goal is to raise security while keeping expenses minimal. In the video, even shows he used a little gadget attached to a QuickCharge USB battery bank to get a portable 12 VDC source suitable for tripping these locks. Which, interestingly enough, is based on a trick he read about in the Hackaday comments. Something to consider while penning your next comment on these storied pages. Then, you could change the password of the Administrator user, for example.