Content
The fabric also has a multi-party, single queue system utilising Kafka, providing failover, but theoretically allowing the party with the fastest server to cut as many blocks as they wish. Gospel can support both these methods if customers wish as, for most purposes, one or both of these offer a good balance of efficiency and safety in a semi-trusted environment, especially when combined with pre-endorsed transactions. Unlike all these systems, Gospel is a private, permissioned blockchain. That means that nodes can only join with the agreement of the others, preventing the possibility of a 51% attack and removing the need for a brute force algorithm. More recent attempts have centred around Proof of Authority systems which dictate who has the right to cut the next block based on a shared algorithm.
In a transaction primarily a message is broadcasted that just has information, says an X Cryptocurrency from one wallet and credits X coins into another wallet. In Bitcoin, the difficulty automatically adjusts every 2,016 blocks.
Unstoppable Domains Raises Us$4 Million In Series A For Censorship Free Blockchain Domains
Moreover, I do not need to deal with banks or currency conversion because Bitcoin is not a fiat currency. Bitcoin is a digital currency launched in 2009 by an anonymous inventor or group of inventors under the alias of Satoshi Nakamoto . It is the largest cryptocurrency in market capitalization with over 100 billion dollars (Chan et al., 2019; Grobys and Sapkota, 2019; Blockchain.com, 2020).
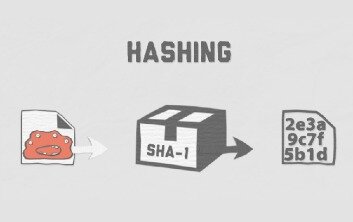
A cryptographic hash is a digest or digital fingerprints of a certain amount of data. In cryptographic hash functions, the transactions are taken as an input and run through a hashing algorithm which gives an output of a fixed size. Proof-of-Work is a consensus algorithm that is used to validate transactions and broadcast new blocks to the blockchain.
Even if one character in the message is added or deleted, the entire hash value will be completely different. Yet, a certain plaintext will always yield the exact same hash value. The only difference between SHA-256 and SHA-512 is that SHA-512’s hash value is double the length (SHA-256 is 32 bit & SHA-512 is 64 bit). SHA-1 was the original hash function, but was later considered outdated with the release of SHA-2. SHA-2 consists of six hash functions where SHA-256 and SHA-512 are the most popular. SHA-256 takes a plaintext and encrypts it into a sequence of numbers and letters.
Hashing Technology In Blockchain
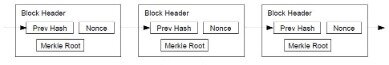
An interesting note is that blockchain does not keep a running balance, each new transaction checks the complete bitcoin history. Blockchain immutability is created with cryptographic hash by creating a new block that contains the hash of the previous block. The 100th block now has the data from the 99th block in hash format, and the 99th block contains the hash of the 98th block. This means each block contains the data of the previous block and also the data of that block. If one block changed we need to change the data and hash of the entire chain. Transaction message needs a signature from the private key from the sender wallet to be valid.
How do I find old block hash?
Hash address of the previous block. Hash of the all the transactions those are part of the current block. Nonce, a random value which can be got using hit and trial method. It is a predermined value and once a right value for the block is found then this block can be added into the blockchain.
The network incentivizes users to participate in the block validation process by assigning newly mined Bitcoins to the first user who randomly finds a hash with a value smaller than the threshold. Presently, after the latest Bitcoin halving, this remuneration is 6.25 Bitcoins or around USD 60,000 at the current exchange rate . For this reason, the hashing process is called “mining” and miners often join to form large mining pools to have a more stable source of income (Gervais et al., 2014). Higher hashrate means more resources are being devoted to process transactions on the blockchain. The block reward, which is a predetermined amount of free coins given to a miner each time a new block is mined, undergoes a programmed halving in order to incrementally reduce the total supply over the course of a coin’s mining lifespan. For Bitcoin, block rewards are cut in half every 210,000 blocks, or approximately 4 years.
In other terms, information is not being shared during the key exchange, but instead both parties are creating the key together. This makes it very difficult for someone to intercept since certain keys have never been presented to the public. AES , which stands for Advanced Encryption Standard, is a 128bit symmetric block cipher chosen by the U.S. government to protect classified information.
Recall that the data we put into a hash function changes the hash output. Therefore changing the nonce or timestamp provides an opportunity to hash the same block of transactions over and over and generate different hash outputs. In the diagram I’ve included a screenshot of the bitcoin wallet mycellium as an example of how a user might interact with a blockchain. Using mycellium a user may create a transaction; a request to send bitcoing from their address to another address. This transaction then enters the ‘mempool’ which can be considered as a waiting room for the transaction to be added to the blockchain. Miners pick transactions from the mempool and create ‘blocks’ of transactions which they then compete with other miners to validate and add to the chain. Before new transactional data can be added to the next block in the chain, miners must compete using their machines to solve a difficult mathematical problem.
Because Bitcoin is not a physical currency, you cannot spend them the same way you would physical cash even though, where to keep bitcoins bitcoin mining math problem cash, transactions are peer-to-peer. Beginners Bitcoin Blockchain It is by way of this semantic true or false programming language that messages are written, and transactions are sent and received successfully. Multiplication is one of the disabled functions, which keeps the script simple in terms of programming. As a node receives incoming blocks from the network, it will validate how to convert litecoin to bitcoin on bittrex adjust poloniex chart blocks and then link them to the existing blockchain. The X11 hashing algorithm created by Dash core developer Evan Duffield. Get an ad-free experience with special benefits, and directly support Reddit. Take a look at the below image and you will see a few familiar items like hashes of keys and opcodes running the program.
Hiveon Pool Vs Nicehash
The main idea was that all participants through voting could decide where the capital acquired at the ICO stage will be invested, which put more control in the investors’ hands. When the user sends ether, they are able to interact with these self-operating computer programs, which will run the code without errors. Ethereum allows developers to build thousands of different applications that go beyond anything built on a blockchain before. Ethereum is an open software platform, which was constructed in 2015 by Vitalik Buterin, using the blockchain platform that allows consumers and companies to build decentralized applications. Soft forks are software updates to a digital asset blockchain, which do not result in a physical split of the blockchain into two digital assets. A fork is a condition where the state of the blockchain diverges in two different chains where one chain operates by different rules and the other. This can occur due to a discovery of a bug, upgrading features of the blockchain, and changes to the node software.
- As the value of the cryptocurrencies has risen, so has the value of the reward, increasing the amount of computing power miners are willing to dedicate to it.
- You might think, for example, that each bitcoin would be worth the same as every other bitcoin – that, after all, is how money is supposed to work.
- It was one of the five finalists of the AES contest, but itwas not chosen as the standard.
- Because hashing algorithms are incredibly difficult to “hack,” even for emerging quantum computers, Bitcoin’s blockchain is extremely secure.
- That means if all of the operation codes are satisfied, and the addresses and keys also match, then the transaction is approved, and added to the blockchain.
- In a hard fork, the data on the new chain is a duplicate of the old chain.
The public key is distributed to anyone and with that public key, they can encrypt a message, once encrypted, the only way to decrypt that message is by using the corresponding private key. This process helps in reversing the encrypted message into its original format. Cryptography is a protocol that prevents the third party from accessing the information or data of the user.
Blockchain Address 101: What Are Addresses On Blockchains?
Party B uses a cryprography function along with their private key to unencrypt the data. This encrypted data can now only be unencrypted by party Bs private key. The following diagram shows how one party can encrypt a document, then send it across a public network, where it can be decrypted by another party. In this diagram, pk represents a person’s public key while sk represents their private/secret key. Each person has their own key pair that they will generate, they will only share or publish their public keys. A 256-bit number is simply a number that when written in binary has 256 digits.
So if miners are finding bitcoins more often than every 10 minutes on average, the difficulty moves upward. If miners are finding bitcoins less often than every 10 minutes on average, the difficulty moves down. Miners are motivated to do all this in search of monetary rewards. In the process, though, they play a key role in securing cryptocurrencies, most famously Bitcoin, by making it more difficult for attackers to gain a 51% majority control over the blockchain network. Since each hash created is completely random, it can take millions of guesses – or hashes – before the target is met and a miner wins the right to fill the next block.
Mind Your Ps And Qrs: A Guide To Avoiding Cryptocurrency Scams
Don’t forget there is a capped supply of only 21 million, and as the world’s appetite for bitcoin grows, so will it’s price. At the time Sebastian first got his hands on BinBotPro it was going through its first round of beta testing, so he was able to test it out fully without paying a dime.
The message is converted into an array of numbers and letters through an algorithm and even a change of one letter creates a significantly different hash value. Bitcoin is stored and transferred digitally in a virtual wallet and unlike cash, each bitcoin has a public transaction history that makes it theoretically impossible to counterfeit.
As the value of the cryptocurrencies has risen, so has the value of the reward, increasing the amount of computing power miners are willing to dedicate to it. This has led to rampant electricity consumption, with Bitcoin alone being estimated to consume 2.55GW of energy late last year, which could be annualised to 22.3TWh. This is not far from the amount of energy consumed by the whole of Ireland.
Now the entire concatenated string is hashed again and perform a difficulty level comparison. There is a number of Hash functions available, of these following, are the majorly used hash functions in Blockchain technology. You should start receiving payments every day which you can withdraw in bitcoin or sent directly to your bank account. BinBotPro is holding their final round of beta testing and is currently looking for people to help out in testing their software.
The blockchain could thus fragment – ‘fork’, as a miner would put it – into multiple competing versions. When a bitcoin user initiates a transaction, their computer system dispatches a message embodying the transaction to other computers in the bitcoin network. Those systems retransmit the message, and eventually it reaches all or nearly all of the network. (Because there’s no central server, there is no way of broadcasting a message directly to the entire network.) A miner’s computers gather these messages together into a block of around two thousand transactions, ‘hashing’ them as they go. A hashing algorithm takes a message, scrambles it thoroughly, and condenses it into a relatively short, fixed-length form called a ‘digest’.
So traders are able to run trading software from their home computers and profit in their sleep. The phenomenon of running automated software to trade cryptocurrencies and generate money online is not new. Nevertheless, recently these programs have managed to get a lot of attention because they have become far more accurate and profitable. This iframe contains the logic required to handle Ajax powered Gravity Forms. The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation. Distributed systems and Blockchains can be secured through several other mechanisms that do not require computationally intensive proof of work.
These numbers are commonly used in cryptography and blockchain as they are hard to guess. To understand the concept of blockchain and the terminology involved we need to understand some number formats from mathematics and technology.
The default fees are calculated as a simple function of the size of the transaction in bytes. At present the fee is 0.0005 BTC (around 5¢) per thousand bytes, so from the sender’s point of view it’s negligible. To a miner, however, the potential cumulative income from hundreds or thousands of transaction fees isn’t to be sniffed at. In fact, the only known way to find one is to test billions of numbers until you happen to find one that produces a valid hash. Just a database but with cryptography, immutability and transparency benefits. Large number of participants protects the network; the higher the number the better. 4) The attacker goes online, as they have the longer chain the rest of the network will trust it and 5) they can then double spend.
Because SHA-256 hashing is such a simple operation, it is possible to design and have someone build a chip that has many separate processor circuits, each of which hashes independently of the others. The chips that power its mine in Inner Mongolia, are of its own design, and are manufactured by the Taiwan Semiconductor Manufacturing Company, owner of the world’s largest silicon-chip foundry. Each of Bitmain’s Antminer S9 machines contains 189 of these ASICs; each of these ASICs, in turn, has more than a hundred separate little SHA-256 processor units hardwired into the chip. Nowadays, given the very demanding nature of the goal, it’s usual to find that not a single one of these nonces will work.









